How the Anapaya GATE protects your mission-critical infrastructure

February 29, 2024

The Internet is a marvel of technical ingenuity and permeates almost every facet of our daily lives. The ability to connect everyone with everything profoundly impacts societal, economic, and political developments - the Internet's openness and flexibility is what enables it to thrive and flourish.
As with many things, the biggest strengths can be the most glaring weaknesses, depending on the context. The Internet's openness also means that all kinds of actors can participate in this global communication fabric. Simultaneously, there is an increasing trend to adopt the Internet as the network for critical infrastructures such as finance, government, healthcare, or utilities.
This trend is driven by various factors, such as the adoption of the cloud by businesses, the growth of the remote workforce fueled by the COVID-19 pandemic, and the increased level of interconnectedness between businesses and their suppliers, partners, and customers. Critical infrastructures are not deliberately choosing to adopt the Internet for their networking needs - they have no other choice.
Exposing these services on a global network constitutes an enormous risk exposure. Obviously, strong authentication mechanisms and encryption can be used to limit access to data on an application level; however, on the network layer, these services are still exposed to various kinds of attacks, e.g., Distributed Denial of Service (DDoS) attacks or remote exploitation of vulnerabilities of the exposed service.
Challenges in networking security and the need for innovative solutions
Today, there are various types of mechanisms to deal with these network security issues. Network administrators can place a firewall in front of a critical service to keep out undesired traffic according to rules and heuristics. However, it is impossible to reliably deny undesired traffic from reaching your service. Furthermore, firewalls themselves can be vulnerable to remote exploitation, and finally, firewalls cannot cope with denial of service attacks as they simply get overloaded.
To defend against DDoS attacks, businesses have a variety of options available, but they all work in a similar fashion. Through network-level mechanisms (usually BGP-based or DNS-based), traffic gets routed through so-called "scrubbing infrastructures" that classify packets into legitimate and undesired ones and only forward the legitimate packets towards the service.
Due to the dimensions of these scrubbing infrastructures, they can process enormous amounts of packets - usually much more than the operator of the service that is protected by the scrubbing infrastructure. However, the classification into legitimate and undesired packets is imperfect at best and the cost of such a solution can be prohibitive.
Protecting mission critical services with Anapaya GATE
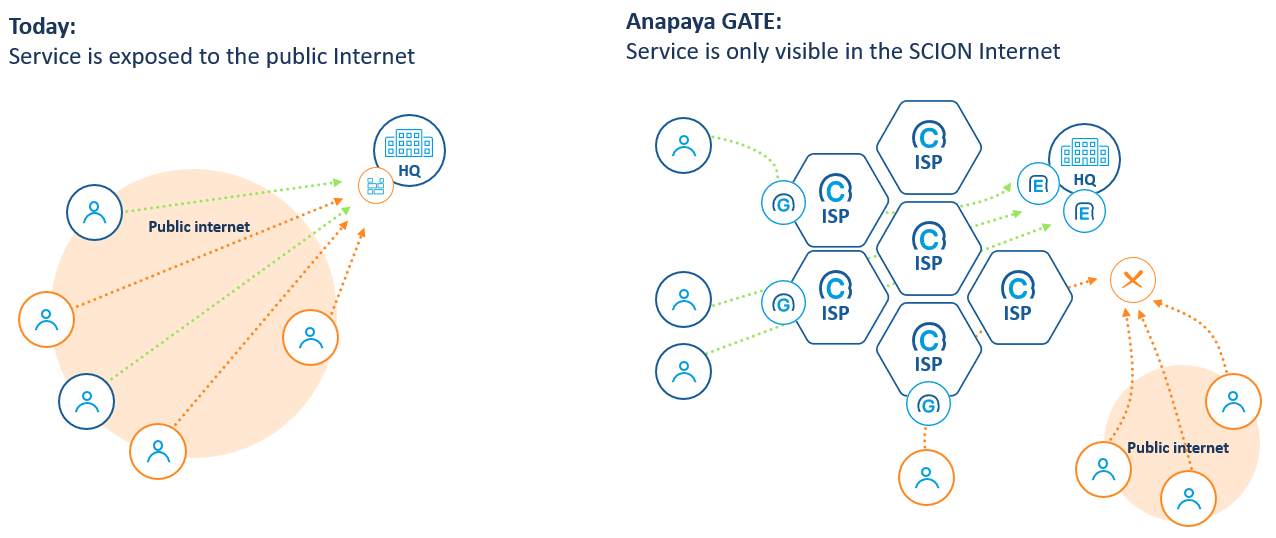
Today, a service that needs to be accessible beyond the internal network infrastructure of an organization will inevitably be put on the Internet - there is simply no other option. This also means that, without any additional measures, the service can be accessed by everyone and everything. The mechanisms mentioned above are then used to keep out undesired actors - a form of blacklisting.
In that regard, the Anapaya GATE service based on SCION technology introduces a paradigm shift - it enables operators of critical services to have fine-grained control over where their services are visible on the network. The question becomes who to let in instead of who and what to keep out.
How Anapaya GATE and EDGE work to safeguard your critical infrastructure
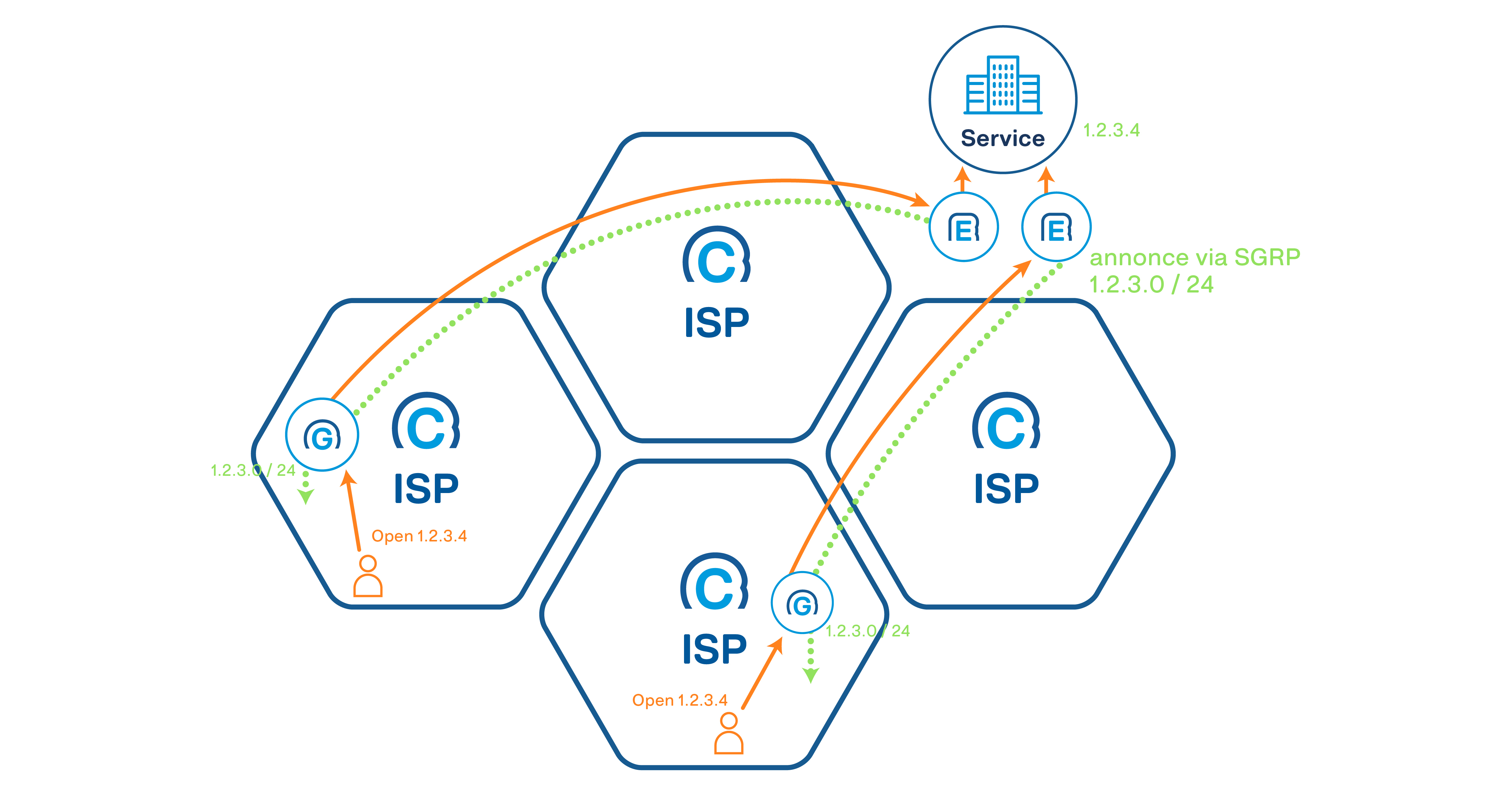
First of all, the protected service needs to be connected to the SCION Internet. The best way to achieve that is by installing an Anapaya EDGE gateway (EDGE), ideally in a redundant configuration. The Anapaya EDGE gateway is the premier way of connecting networks to the SCION Internet. The primary purpose of the EDGE is to encapsulate standard IP traffic within SCION packets (IP-in-SCION tunneling). That way, the EDGE enables any application to transparently use the SCION Internet without any changes to the application.
The secondary purpose of the EDGE is to make optimal path decisions enabled through SCION's source-selected path architecture. In a redundant configuration, two EDGE gateways are connected to two independent SCION Internet Service Providers (ISPs), which, combined with the EDGE's multipathing capabilities, leads to an extremely resilient setup.
This covers the connectivity on the service side. Obviously, the service needs to be accessible to its target audience, i.e., end users and clients in selected SCION ISPs. This is where the Anapaya GATE (GATE) comes into action. The GATE is a carrier-grade SCION gateway infrastructure that enables end users and clients in a GATE-enabled SCION ISP to connect to services within the SCION Internet. Technically, the GATE offers the same IP-in-SCION tunneling functionality as the EDGE - just on a much larger scale.
The EDGEs on the service side are now configured to establish IP-in-SCION tunnels to the GATEs of selected SCION ISPs. This is the first decision point for the service operator - only through GATEs to which a tunnel has been established can the service be reached. By carefully selecting the GATEs the service operator can greatly limit the exposure of its service - from the global Internet to just the selected GATEs.
Through the SCION Gateway Routing Protocol (SGRP), the EDGEs and GATEs exchange IP reachability information, which then gets injected into the ISPs network. This way, end users and clients in a GATE-enabled ISP can reach the protected service without any changes required on the client side, neither on the network nor on the application layer.
The benefits of limiting service exposure
First and foremost, a protected service exposed through the GATE infrastructure exhibits a tremendously reduced attack surface compared to a service exposed to the global Internet. This holds especially true if the protected service has a focused target audience, e.g., limited to a specific country or region. Take the example of Switzerland: A service that needs to be available primarily in Switzerland benefits greatly from having its reachability limited to Swiss networks rather than the entire Internet. But when a service needs to offer global accessibility, the GATE setup has limited impact to reduce the attack surface.
Exposing a service via the Anapaya GATE has the following benefits:
- A greatly reduced risk of suffering a successful DDoS attack on the protected service or its access infrastructure simply because the reachability is limited to a surgically selected set of networks.
- A greatly reduced risk of being targeted by remote exploitation attempts, due to constrained reachability and thus the protected service being "invisible" to many of the common attack sources.
- A highly resilient access infrastructure through the Anapaya GATE’s multipathing capabilities combined with the diverse SCION Internet backbone providing many independent network paths from the source to the destination and back.
It is clear that the Anapaya GATE itself is not a panacea against all kinds of denial of service or intrusion attacks. An attacker that is part of a network where the protected service is exposed can still attempt to find exploitable vulnerabilities; for example, if the protected service is not provisioned well enough to handle the load coming from the selected source networks, it can still be brought to a standstill.
However, protecting a service through the Anapaya GATE provides an efficient, simple, and low-cost defense mechanism that can complement and improve other defense mechanisms. For example, firewalls can be much smaller provisioned since the amount of traffic they will need to handle is drastically reduced by limiting the exposure of the protected service through the Anapaya GATE.
Controlling exposure in the SCION Internet
But what if the SCION Internet becomes as big as today's Internet? Does the point about a reduced attack surface still hold? The answer is a resounding yes! Within the SCION Internet, each network has control over what other entities can get access to path information leading to the network. To explain this in more detail we need to make a little detour of how path exploration and path dissemination work in SCION.
SCION paths are created by propagating the so-called Path-Segment Construction Beacons (PCB) through the SCION network - from the core towards the leaves. Amongst other things, these PCBs collect the routing information needed to send a packet along a SCION path. Individual networks then register selected path-segments with the public SCION path-segment directories to make them available to everyone who wants to establish a communication path to said network. Now, a network can also decide not to register their path-segments with the public SCION path-segment directories and instead keep them "hidden" - so-called "hidden paths". These hidden paths can then be distributed to the desired networks, e.g., by using a hidden path infrastructure, ensuring that only those networks have access to the said path information.
Coming back to the original question of whether the attack surface can also be reduced if the SCION Internet is as large as today's Internet, we can now see that the operator of the protected service can ensure that their path information is only accessible to exactly the desired GATE provider networks and thus effectively limiting the exposure of the protected service to exactly those networks and no more.
Use case: Hiding VPN server infrastructure
With the sharp increase in the number of employees working remotely - largely driven by the COVID-19 pandemic, organizations have been rushing to implement the means for their remote workforce to securely and reliably access the resources necessary to perform their work. Quite often this remote access is implemented using a Virtual Private Network (VPN) solution.
In such a setup, the organization runs the VPN server infrastructure in a data center, and employees first establish a VPN connection to the central VPN server before they can access any of the resources. The VPN server infrastructure is necessarily exposed to the Internet because employees need to be able to connect to it from their homes or on the road.
Obviously, the VPN server infrastructure is a highly critical component of the organization. A successful denial of service attack on the VPN server for multiple hours or even days could mean that the productivity of the organization plummets since their employees cannot connect to the necessary resources to perform their work anymore. Furthermore, the VPN server is also a potential entry point for intruders into the internal infrastructure of the organization.
One observation is that for many organizations, the vast majority of employees do not need to connect from anywhere in the world but from relatively few networks. Such is the case for a prominent Swiss financial institution. The bank's employees are 95% based in Switzerland, and thus, their main VPN server infrastructure does not need to be exposed to the entire Internet. Instead, they opted to put their VPN server behind the Anapaya GATE service provided by multiple Swiss SCIONabled ISPs, thus only exposing the VPN server infrastructure within Switzerland.
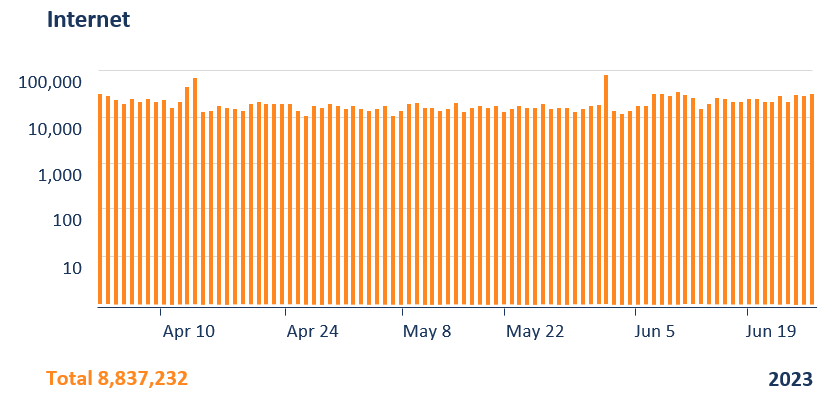
Attacks with unspecified intent
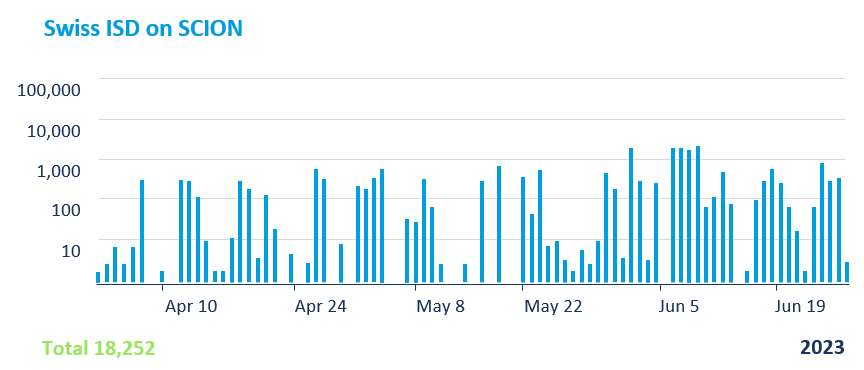
Attacks with malicious intent
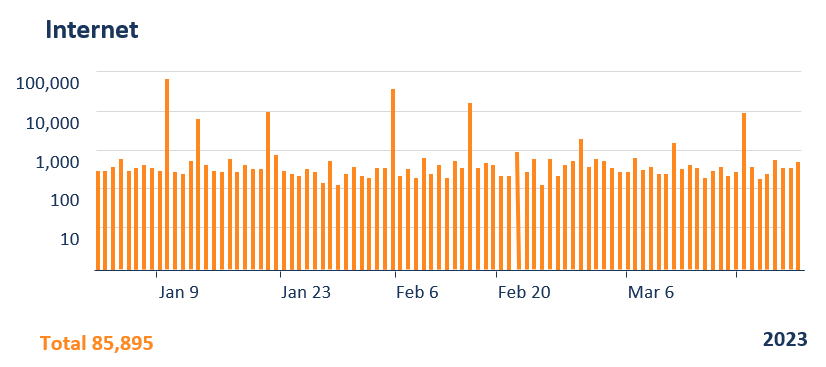
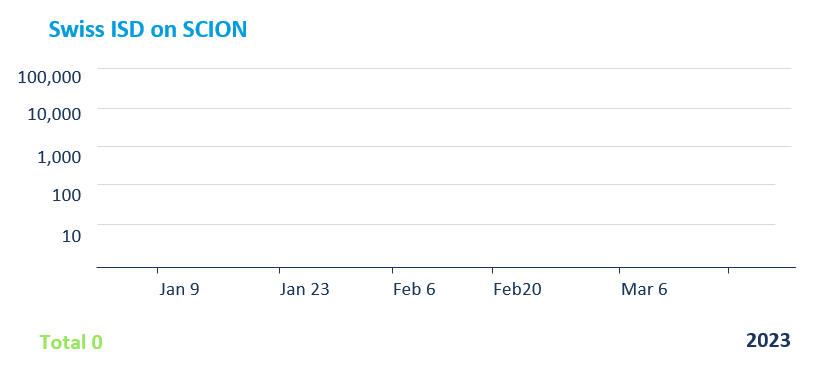
The results are remarkable - the bank collected traffic on their Internet-facing and GATE-protected VPN servers over a time period of one quarter. They then classified the illegitimate traffic into flows with "unspecified intent" - basically port scanning, device fingerprinting and user mistyping their login credentials - and flows with "malicious intent" - actual attack payloads. For both categories the numbers show a tremendous reduction of illegitimate flows to the point where there were no traffic flows with malicious intent on their GATE-protected VPN server.
Use case: Protecting public web services
Another use case is the protection of a public web service that has a focused target audience, for example the portal of a Swiss healthcare provider. Presumably, the vast majority of the users of the portal are based in Switzerland. This makes it a perfect fit for the Anapaya GATE service. The healthcare provider can put their web portal behind the Anapaya GATE service provided by multiple Swiss SCION-enabled ISPs, thus only exposing the web service within Switzerland.
However, the portal might still need to be available outside Switzerland, for example for users traveling abroad. In this case, the healthcare provider can still expose the web portal to the Internet, effectively using it as a fallback mechanism to users that are not within the reach of the selected Anapaya GATE providers.
Under normal conditions, the effect of this setup is not visible to the end user. However, in case of any attack, e.g., a DDoS attack on the Internet-facing web portal, it can simply be disconnected while the vast majority of users still have access to the web portal through the Anapaya GATE service. This is an extremely powerful mechanism to ensure the availability of a critical service even under attack.
There are a variety of ways to expose the service simultaneously via the GATE service and the public Internet depending on the use case, e.g., by using DNS-based or BGP-based mechanisms. The simplest solution however is to connect to one of the GATE providers that offer access to the public Internet through their GATE service. This way, there is only a single access point to the service, and the service operator can dynamically control on their Anapaya EDGE gateways from which GATE providers the service is reachable.
Why is GeoIP filtering not enough? |
|
| GeoIP filtering is a common method to limit the exposure of a service to a specific region. However, GeoIP filtering is not a reliable method to limit the exposure of a service. The reason is that GeoIP databases are not always accurate, due to unreliable data sources, IP address blocks being transferred from one entity to another, and infrequent updates to those databases. Furthermore, GeoIP filtering is often happening on the application layer when the traffic has already reached the service, and thus does not protect the service from being overwhelmed by illegitimate traffic. |
Conclusion
Protecting a service through the Anapaya GATE provides an efficient, simple, and low-cost defense mechanism that can complement, improve, or even replace other defense mechanisms. For example, firewalls can be much smaller provisioned since the amount of traffic they will need to handle is drastically reduced already by limiting the exposure through the Anapaya GATE. Furthermore, a dedicated DDoS mitigation solution might not even be necessary.
If you are interested to learn more about how the Anapaya GATE can protect your critical infrastructure book a demo with our specialist!
