The U.S.A.’s biggest web service for health care payments that handles some 14 billion transactions a year is struggling to recover from a cyberattack. The vital system is operated by Change Healthcare and took a hit from a ransomware attack carried out by the Blackcat/ALPHV ransomware group as confirmed by Change Healthcare. The Change Healthcare attack underscores the urgent need for enhanced cybersecurity measures across mission-critical infrastructures to prevent similar disruptions.
Change Healthcare maintains the health care’s pipeline — payments, requests for insurers to authorize care, and much more. Their system was down for nearly a month after the February 21st attack, severing its digital role connecting providers with insurers in submitting bills and receiving payments.Beyond financial losses, a huge human impact
This ransomware healthcare attack sent the US health care system into a downward spiral — costing providers an estimated $100 million daily as payment disruptions continued after the initial attack as reported by CBS.
The interconnected nature of digital services in our society has a huge impact on our daily life. When this interconnectedness comes under threat, it tends to be a damaging impact – with ripple effect.
The repercussions have not just been enormous in their nationwide reach and extended financial losses, some of them damage patient care. Pharmacies, health clinics, hospitals and patients have been left in a bureaucratic/paperwork chaos that left them unable to proceed with handing out prescriptions, performing check-ups, responding in time to medical emergencies or receiving medications and undergoing treatments; the list goes on. In short, it exposed patients to data theft and even medical error – interrupting patient-relevant outcomes, some of which were extremely time-critical. This was obviously an attack meant to destabilize the health care sector, as previously seen last year in Britain and purportedly carried out by Blackcat.
With this case exposing healthcare data security challenges while gaining international media attention, including the biggest mainstream outlets, and the American Hospital Association labelling the breach “the most significant and consequential incident of its kind against the U.S. health care system in history,” I deemed it worth stopping and reflecting about what could have been done differently – as a leader as well as a SD-WAN expert with over two decades of experience in cybersecurity.
What we know is wrong and why
The internet is the network of choice to conduct business, especially across critical infrastructure. Today, a service that must be accessible beyond an organization's internal network infrastructure will be put on the internet as there is no other option.
Critical infrastructure is not meant to use the internet as the network of choice. Bot more often than not, there is just no other choice to reach the audience.
When a web service is on the internet, it can be accessed by everyone, everywhere. That’s very much the superpower of today's internet. And while the openness and interconnectedness of the internet is a beautiful thing, it also comes with a massive attack surface, posing a risk not only to the service itself but also the wider network of a corporation – attackers use the internet to attack an exposed service. And once attackers are in, they might find ways to spread deeper into the corporate network, jeopardizing data and disrupting operations.
While certain cybersecurity measures like strong authentication mechanisms and encryption can be used to limit access to data on an application level, on the network layer, services are still exposed to various kinds of attacks, e.g., distributed denial-of-service (DDoS) attacks or remote exploitation of vulnerabilities of the exposed service, like in this specific scenario.
Even the “healthcare and public health sector-specific cybersecurity performance goals” from the Department of Health and Human Services (HHS) fall short of addressing the elephant in the room. Namely, the network itself – in all cybersecurity defense best practices illustrated, it is the traditional internet on the other side of any firewall. We need to become less defensive, less reactive – and take more initiative in our measures to mitigate cybersecurity risks.
And how do we go about that? We need to empower each other with the right set of tools to reduce attack surface to begin with. Namely, ensuring business services run on a reliable network.
There is a real-world urgency in getting such critical services on a network that is not as susceptible to these malicious intrusion attacks as they are today. Known or not, the exploited vulnerability in Change Healthcare’s web service could have benefited from a reduced attack surface. In the twenty years I’ve been active in the cybersecurity industry, it never ceases to amaze me that the risk of the attack carried out against Change Healthcare in the States one month ago could have been significantly lower were the right prevention framework in place. Certainly, the magnitude of its ripple effect could have been greatly reduced.
The repercussions of this attack are still ongoing, and it is devastating not just for the web service attacked but all businesses and people who have relied on it. One paper reporting on similar but smaller ransomware attacks on the health care industry in the States from 2016 to 2021, published last autumn, stated that “ransomware attacks decrease hospital volume by 17-25% during the initial attack week, reducing revenue even further. [Ransomware attacks] increase in-hospital mortality for patients who are already admitted at the time of attack.”
Reducing web service exposure to mitigate attack risk
Reducing attack surface may seem an overly obvious approach. However, the implementation of such strategies is not ipso facto simple. Most attempts try to fortify the exposed services or entry doors with more – and smarter – filters or improved identification algorithms. Usually, we end up with more complexity, tougher operational challenges and, potentially, new vulnerabilities.
A better way forward is to make sure that threat actors cannot see you to begin with. This is what a network like SCION makes possible: SCION was introduced in 2015 and offers route-based interdomain communication. That’s not groundbreaking per se. Route-based communication is not new and is well-known for its security properties. But it IS groundbreaking in the context of the internet. No route to a target means no visibility; this means it is not possible to attack a target – thereby ensuring healthcare network security.
With a network of only trusted ISPs in place and accessible for their users only via Anapaya GATE, you control the attack surface of any of your mission-critical services that are exposed to the internet. And surely, it is fundamentally more secure to announce your service only to your audience than to have the same service exposed to the entire worldwide internet.
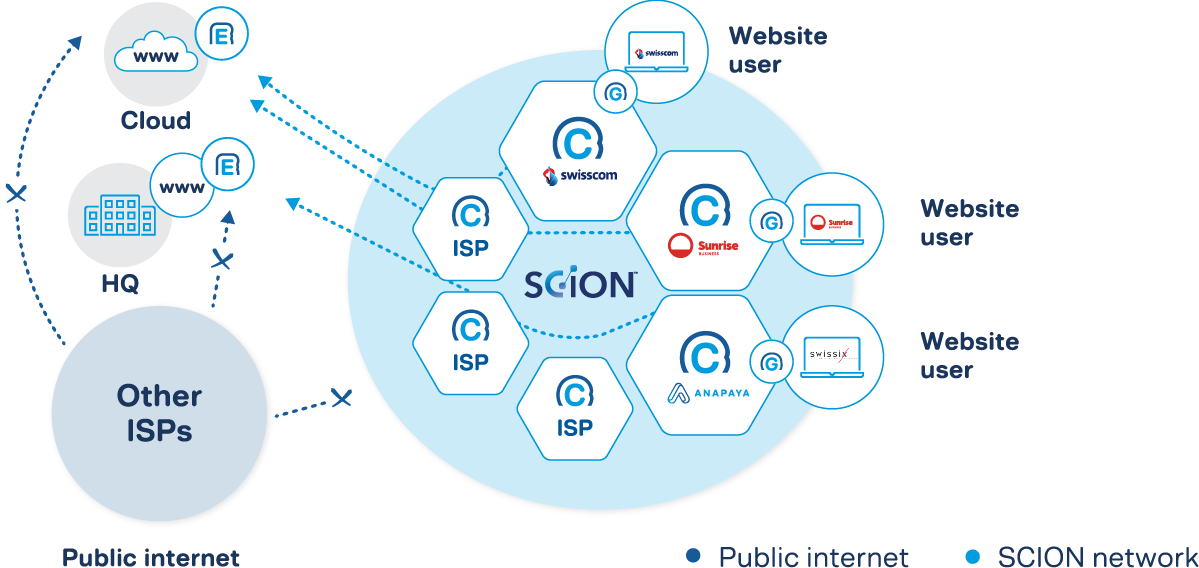
The Change Healthcare debacle can be seen as a network scenario where Anapaya GATE would have been useful. With the majority of its users based in the US, the healthcare provider could put their web portal behind the Anapaya GATE service provided by multiple SCION-enabled ISPs: exposing the web service only to select users – giving them more control over who accessed the web service. And, in the case of such a disruption or attack, Change Healthcare could have closed the entry point to the service while quickly identifying the perpetrators by their IP address.
With the service only visible to selected SCION-enabled ISPs and their users, the exposure of the network would have been limited – making it easier to prevent intrusion attacks from the onset. Therefore, it would have been unlikely that the ransomware group Blackcat, their affiliates or any other threat actor, for that matter, would have seen the service – unless they were a selected user of that network. As we know, what cannot be seen cannot be attacked.
The magic of such a solution is less in the concept, but more in the fundamentally new way of how it is being implemented.
The good news is that this particular kind of solution has been validated: we documented the number of attacks perpetrated against a Swiss financial institution in Switzerland for a quarter in 2023. During that time, they suffered 8M+ attacks with unspecified intent and 85K+ attacks with malicious intent on their VPN infrastructure.
Benefiting from the fact that most of their workforce is in Switzerland, they also decided to put their VPN behind the GATE provided by multiple Swiss SCION-enabled ISPs, meaning they only exposed the VPN server infrastructure within Switzerland and within selected ISPs.
During the same period, they identified only 18K+ attacks with unspecified intent and 0 attacks with malicious intent on SCION via Anapaya GATE. And by being in control of the attack surface, every single identified attack comes with an ID and can be pursued.
To control the attack surface and to be in control of who can get my route information is powerful, but it becomes extremely powerful and a security force multiplier in the context of the public internet.
A service that needs to be available primarily in the US benefits greatly from having its reachability limited to US networks rather than the entire internet, from both a technical and legal point of view. When a service needs to offer global accessibility, however, the GATE has a curbed impact in reducing attack surface.
It is clear that Anapaya GATE by itself is not a final measure to prevent all kinds of intrusion attacks. However, protecting a service through Anapaya GATE provides an efficient, simple and effective prevention mechanism.
Call to action: rethink and reinforce cybersecurity for critical infrastructure
The consequences of the cyberattack Change Healthcare suffered are human – ability to access and pay for care is a primary need. Business leaders and decision-makers in critical infrastructure face lost trust in addition to lost revenue.
The FBI's annual Internet Crime Report confirms that health care and public health were the top sectors impacted by ransomware in 2023. Health care systems need to realize that even if cybersecurity defenses are succeeding today, they may not be effective in the future. We must consider not just how we detect threats, but how to prevent healthcare data breaches before they happen. SCION and Anapaya GATE offer network-level protection, ensuring better data security in healthcare and greater system resilience.
With more and more attacks targeting critical infrastructure, the leaders at the helm are at a turning point where peace of mind is challenged on a daily basis and the consequences of mistakes come at a personal and professional cost. It’s time to challenge the status quo and adopt advanced cybersecurity measures.
Businesses leaders need to look for solutions that are sustainable and strengthen their network exposure to protect the impact disruptions can have on humans.
Critical infrastructure decision-makers need to explore proven yet innovative solutions that might require change in behavior but that also bring benefits along the way. With a network like SCION, leaders in such industries would have more control over risk management and thereby gain peace of mind, knowing they are doing everything they can to protect the human factor.
I invite all leaders to rethink the status quo – a solution such as Anapaya GATE on SCION presents a compelling alternative. New technologies are for and by humans – to make all our lives better. Let’s embrace the change now.





.png?width=380&name=Image%20(11).png)




