As the medical industry becomes more reliant on digital systems, the need for strong cybersecurity solutions becomes increasingly important. The prevalence of cyberattacks targeting the medical sector is alarming, with the Office for Civil Rights reporting a staggering number of incidents in recent years. In 2022 alone, there were 569 cyberattacks on the medical sector, with a significant portion targeting network servers. Among these attacks, hacking and IT incidents accounted for 453 cases, highlighting the severity of the situation.
But the implications of cyberattacks in healthcare extend far beyond mere data breaches. They directly threaten patient safety, compromise confidentiality, and disrupt vital operations within healthcare organizations. Not to mention, the financial and reputational damage incurred as a result of these attacks often has long-lasting consequences.
In this blog post, we'll look at the current state of cybersecurity in healthcare, discuss its various risks, and explore ways to protect patient data. Finally, we will examine the role of Anapaya in safeguarding healthcare organizations from cyber threats.
Why is cybersecurity important in healthcare?
To understand the importance of cybersecurity in healthcare, it's essential to pay attention to what makes the medical sector particularly susceptible to cyberattacks:
The extensive and vulnerable attack surface
Healthcare organizations possess a wide and often inadequately protected attack surface. In addition to the common attack vectors faced by all enterprises, healthcare entities must contend with a range of connected medical devices (known as the Internet of Medical Things or IoMT).
They also use personal endpoints, like smartphones or tablets, that may lack sufficient security in healthcare facilities (also known as Bring Your Own Device or BYOD). If we add the presence of multiple third parties with access to sensitive patient data and critical assets within hospital settings, it's easy to see why healthcare organizations are particularly vulnerable.
Moreover, the rapid implementation of remote work and virtual doctor's visits (telehealth) during the COVID-19 pandemic has introduced further opportunities for attackers, often leveraging hastily deployed, inadequately secured IT infrastructure.
A high value of personal health information (PHI)
Personal Health Information (PHI) holds significant value on the black market, far exceeding the value of a stolen credit card number. Unauthorized access to PHI can enable hackers and identity thieves to commit insurance fraud, extortion, identity theft, and other malicious activities.
Material damages and ransomware payments
Breaches in healthcare organizations have tangible and detrimental consequences, prompting victims to be more willing to pay attackers to regain control. For example, disruptions in the operations of healthcare facilities and the unavailability of patient data required for critical procedures can result in potential loss of life.
Additionally, privacy regulations such as HIPAA impose significant fines for disclosing PHI. Penalties for HIPAA violations related to privacy, security, breach notification, and electronic healthcare transactions can reach staggering amounts, up to $1.81 million per calendar year.
Common types of cybersecurity attacks in healthcare
To remain protected from cyber threats, healthcare organizations must be aware of the different attacks they face. Some of the most common ones include:
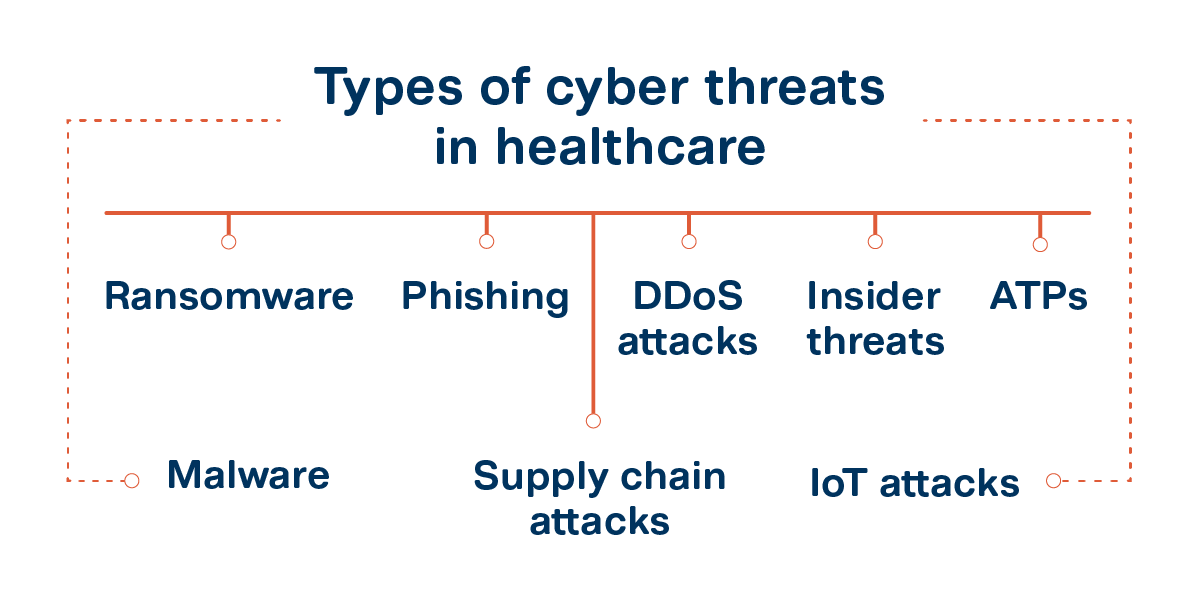
Ransomware
This type of attack involves encrypting data on a computer system, rendering it inaccessible until a ransom is paid to obtain the decryption key. Ransomware attacks can have severe consequences, as seen in the case of CommonSpirit, a hospital in Chicago, where the data of 623,000 patients was compromised.
Phishing
Cybercriminals often use phishing emails or messages that appear to be from legitimate sources, such as healthcare organizations or trusted vendors. By tricking recipients into revealing sensitive information or clicking on malicious links, attackers gain unauthorized access to systems and data.
Distributed Denial-of-Service (DDoS) attacks
DDoS attacks overwhelm target systems with a flood of traffic, rendering them unavailable to legitimate users. This can disrupt healthcare services and divert the attention of IT staff, creating opportunities for other malicious activities.
Insider threats
Insider attacks occur when individuals within an organization misuse their access privileges. This could involve a disgruntled employee or contractor compromising sensitive information, engaging in data theft, system sabotage, or accidentally exposing patient information.
Advanced Persistent Threats (APTs)
APTs are sophisticated, targeted attacks aimed at gaining long-term access to a system. These attacks involve multiple stages and tactics, such as spear-phishing, malware, and social engineering, making them challenging to detect.
Malware
Malware is malicious software designed to harm computer systems by stealing data, disrupting services, or damaging hardware. Healthcare organizations can fall victim to malware through email attachments, malicious websites, or infected software downloads.
Supply chain attacks
Targeting third-party vendors or suppliers, supply chain attacks exploit vulnerabilities in the supply chain to gain unauthorized access to a target network or deliver malware. This poses significant risks to healthcare organizations that rely on external services and software.
Internet of Things (IoT) attacks
With the increasing use of connected medical devices and sensors, healthcare IoT cybersecurity has become crucial. Many IoT devices, such as IV pumps and VoIP systems, may have weak passwords, making them vulnerable to attacks.
By understanding the types of attacks healthcare organizations face, they can prepare and implement robust security measures to protect patient data and ensure the continuity of critical healthcare services.
How to prevent and respond to cyber threats
According to an analysis by the HIPAA Journal, the data reveals a concerning trend in healthcare data breaches over the past 14 years. In fact, 2021 marked a significant milestone, recording the highest number of reported data breaches since the Office for Civil Rights (OCR) began publishing records.
However, there was a slight decrease in reported breaches in 2022, marking only the second instance of a year-over-year decline. Whether it's just a coincidence or a new trend, healthcare organizations must stay vigilant and proactively prevent cyber threats. To mitigate risks and safeguard patient data, healthcare organizations should consider the following best practices:
Develop a robust security culture |
Foster a security-first mindset among employees at all levels of the organization. Promote awareness of cybersecurity best practices, encourage reporting of suspicious activities, and emphasize the shared responsibility of protecting sensitive data. |
Implement strong access controls |
Limit access to critical systems and sensitive data on a need-to-know basis. Enforce strong password policies, implement multi-factor authentication (MFA), and regularly review and revoke access privileges for employees, contractors, and third-party vendors. |
Regularly update and patch systems |
Stay vigilant in applying software updates and security patches to address known vulnerabilities. This includes not only operating systems and software applications but also medical devices and Internet of Things (IoT) devices connected to the network. |
Secure network infrastructure |
Strengthen your defense strategy with a cutting-edge network layer. Implement advanced tech for access control, analytics, policy-based routing, fast failovers, and robust security measures like endpoint/web/wireless security, firewalls, VPN encryption, and more. Elevate your network's security and resilience. |
Conduct employee training and awareness programs |
Educate employees on the latest cybersecurity threats, such as phishing and social engineering, and provide training on identifying and responding to potential risks. Regularly reinforce these training programs to ensure employees stay updated. |
Encrypt sensitive data |
Employ encryption techniques to protect sensitive data both at rest and in transit. Encryption renders the data unreadable to unauthorized individuals, significantly reducing the impact of a data breach or unauthorized access. |
Back up data regularly |
Maintain regular backups of critical data and test the restoration process to ensure data can be recovered in the event of a cybersecurity incident. Store backups securely and separately from the main network to prevent their compromise. |
Establish an incident response plan |
Develop a well-defined incident response plan that outlines the steps to be taken in the event of a cybersecurity incident. This plan should include roles, responsibilities, communication channels, and a clear escalation process to facilitate a swift and coordinated response. |
Engage in continuous monitoring |
Deploy advanced monitoring tools and technologies to detect and respond to cybersecurity threats in real-time. Implement security information and event management (SIEM) solutions to collect, analyze, and correlate security events across the organization's systems. |
Stay informed about emerging threats |
Stay abreast of the latest cybersecurity trends and emerging threats specific to the healthcare industry. Engage with industry associations, participate in information-sharing forums, and collaborate with cybersecurity solution providers to proactively address evolving risks. |
By taking the right steps to protect their systems and data, healthcare organizations can significantly reduce the risks of a data breach or system sabotage, protecting their patients and safeguarding the continuity of their operations. With a comprehensive cybersecurity program, healthcare organizations can protect patient data and ensure that critical healthcare services remain available.
In an evolving threat landscape, time is money
Finally, the first step in preventing a data breach or cyberattack is understanding why it is happening. Cybersecurity is an ongoing process, and healthcare organizations must stay ahead of the curve in understanding and mitigating emerging threats.
Time to detect, respond, and mitigate cybersecurity incidents is of the essence in most cases. The longer an attack goes undetected and unmitigated, the more difficult it is to contain the damage and prevent financial losses. And in the case of healthcare organizations, this damage is not limited to financial and corporate losses. It has a direct impact on the following:
- Patient safety and wellbeing
- The ability to provide uninterrupted healthcare services
- Regulatory compliance
- Data privacy and security of patient information
- Trust among patients and healthcare providers
Given the complexities of the healthcare industry, organizations must prioritize cybersecurity and make it a core element of their operations. Each leaked patient record or compromised company document can have devastating consequences for an organization's reputation and potentially result in legal repercussions.
To establish a robust defense against data breaches, building and fortifying a layered defense system is key. On a network level, SCION (Scalability, Control, and Isolation on Next-Generation Networks) offers an effective solution for protecting the healthcare industry's most valuable data.
By leveraging SCION's capabilities, healthcare organizations can ensure reliable, secure, and stable connectivity and services. By functioning as a private internet exclusively for verified participants, SCION not only empowers healthcare organizations to safeguard highly confidential patient data but also provides a crucial benefit of failover capabilities. In the event of a connectivity failure, SCION seamlessly activates a backup connection, minimizing downtime. This robust failover mechanism guarantees continuous access to critical healthcare systems and applications, enabling healthcare providers to maintain smooth operations and uninterrupted patient care. To discover more about our latest SCION-based network for the healthcare industry, contact us today.
TAGS:
Healthcare, Cybersecurity




.png?width=380&name=Image%20(11).png)




